
Most attack detection still treats applications like interchangeable boxes: requests come in, signatures are matched, packets are inspected, and decisions are made in isolation. That approach worked when attacks were noisy, infrastructure‑level, and largely the same across apps. Today’s attacks are quieter, more targeted, and deeply tied to

Abuse does not always look like abuse anymore. If you run an API or a user-facing application, you may not see traffic spikes or rate limits firing. Dashboards look calm. Everything appears normal. And yet data is leaking, costs are rising, or workflows are being exercised in ways no real

Security is a requirement for any software that runs in production. At the same time, many well-known security tools are priced and designed for large enterprises, with dedicated security teams and complex infrastructure. For startups and small teams, the challenge is different. They need security tools for software that don’
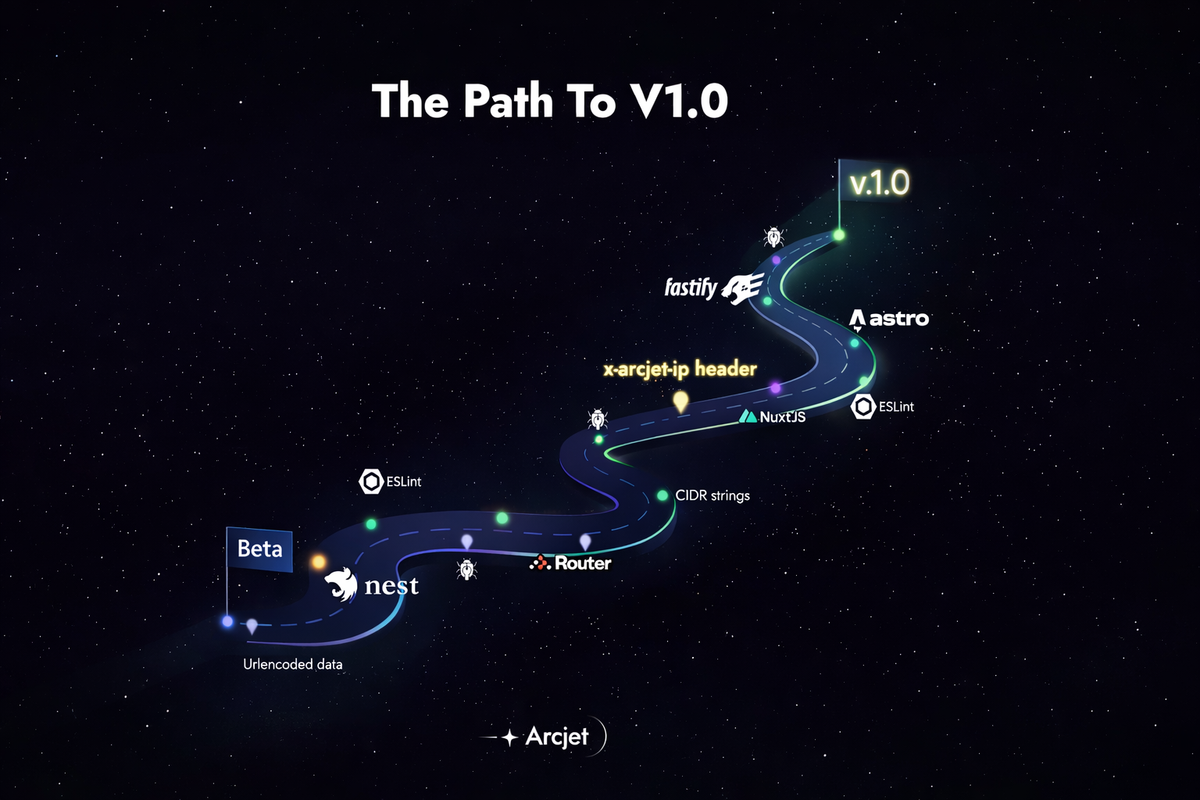
We’ve just released v1.0 of the Arcjet JavaScript SDK. After more than two years of building, testing, and iterating in public, the SDK is no longer beta. The API is stable, production-ready, and something teams can confidently build on. For a security product, that milestone matters for a

Secure Healthcare Data Without Slowing Development A growing number of modern healthcare applications process enormous amounts of patient information through AI, machine learning, and data analytics. That means developers must meet strict compliance standards such as HIPAA, SOC 2, and GDPR, all while keeping their build velocity high. Arcjet helps
At CascadiaJS last year, I gave a talk about a problem I’ve been running into while maintaining Arcjet’s docs: more developers are reading documentation through AI assistants instead of directly on the web. Tools like ChatGPT, Copilot, Cursor, and others now sit between the user and the documentation

2025 was a defining year for Arcjet. We made deliberate progress across product, platform, and company, translating a clear focus into meaningful results. Over the course of the year, we delivered substantial improvements to the Arcjet platform, sharpened our point of view on modern application security, and reached important milestones

The Arcjet Python SDK allows you to implement rate limiting, bot detection, email validation, and signup spam prevention in FastAPI and Flask style applications.

If you search for “Next.js security checklist” or “Remix security best practices,” you’ll find solid guidance. Most framework teams do a good job documenting how to use their tools safely: how to handle authentication, where secrets should live, which APIs run on the server, and which don’t.

The tech stack behind Arcjet: WebAssembly runtimes, a Go gRPC decision API, and region-aware SNS→SQS→ClickHouse pipeline.

How to run Wasm in Java - how does Wasm interact with the JVM and what options are there for Java Wasm runtimes?
How Arcjet detects the real client IP in Firebase deployments, bypassing X-Forwarded-For issues by utilizing a custom Firebase header.

I recently joined James Governor at RedMonk to talk about why security tooling still feels years behind the rest of the developer ecosystem and what it would take to treat security as just another feature that developers build rather than a bolt-on afterthought. You can listen to the full conversation
Arcjet has opened its first physical office in New York City a central hub connecting our distributed team.

Arcjet’s mission is to help developers and security teams build with confidence, no matter where they work or what frameworks they choose. As the web evolves, you need tools that fit the way you already develop. That’s why we’re building native integrations into common web frameworks to

Announcing Arcjet’s local AI security model, an opt-in AI security layer that runs expert security analysis for every request entirely in your environment, alongside our Series A funding.

Arcjet filters let you block requests using expressions over HTTP headers, IP addresses, and other request fields.

How to verify AI agent identity using HTTP message signatures with TypeScript.

Google AI Overviews are causing fewer clicks for some site owners. If this is a fundamental shift in the web's traffic economy, how can site owners control where their content appears?

How we think about open source licensing, releasing open source projects, forks, and contributing upstream.

How do you design a security product for developers when they allegedly don't care about security?

How we implement different layers to secure our developer laptops & environments: Devcontainers, outbound firewall, macOS Transparency Consent and Control framework, and SSH agent for Git keys.

Tips and tools for running a devtools startup remotely in 2025. Document everything. Async workflows. Periodic in-person.

Bots now make up nearly half of all internet traffic - and many aren’t playing fair. Learn how to detect malicious crawlers, distinguish between AI agents, and defend your app using layered bot protection strategies like user-agent verification, fingerprinting, and rate limiting.

How Arcjet uses AWS Global Accelerator to route API requests via low-latency private networking to meet our end-to-end p50 latency SLA of 20–30ms.

How to detect Next.js middleware bypass exploits (CVE-2025-29927 & CVE‑2024‑51479) in request logs and using Arcjet for incident forensics.